 |
| Source |
Assembling a diverse set of public, proprietary, and hand-collected data including dark web conversations in Russian, we conduct the first detailed anatomy of crypto-enabled cybercrimes and highlight relevant economic issues. Our analyses reveal that a few organized ransomware gangs dominate the space and have evolved into sophisticated firm-like operations with physical offices, franchising, and affiliation programs. Their techniques also have become more aggressive over time, entailing multiple layers of extortion and reputation management. Blanket restrictions on cryptocurrency usage may prove ineffective in tackling crypto-enabled cybercrime and hinder innovations. But blockchain transparency and digital footprints enable effective forensics for tracking, monitoring, and shutting down dominant cybercriminal organizations.Wigglesworth comments:
Perhaps. But while it is true that blockchain transparency might enable arduous but effective analysis of crypto-enabled cyber crime, reading this report it’s hard not to think that the transparency remedy is theoretical, but the costs are real.I have argued that the more "arduous but effective analysis" results in "tracking, monitoring, and shutting down" cybercriminals, the more they will use techniques such as privacy coins (Monero, Zcash) and mixers (Tornado Cash). Indeed, back in January Alexander Culafi reported that Ransomware actors increasingly demand payment in Monero:
In one example of this, DarkSide, the gang behind last year's Colonial Pipeline attack, accepted both Monero and Bitcoin but charged more for the latter because of traceability reasons. REvil, which gained prominence for last year's supply-chain attack against Kaseya, switched to accepting only Monero in 2021.Below the fold I discuss both Cong et al's paper, and Erin Plante's $30 Million Seized: How the Cryptocurrency Community Is Making It Difficult for North Korean Hackers To Profit, an account of Chainalysis' "arduous but effective" efforts to recover some of the loot from the Axie Infinity theft.
Cong et al argue that:
A one-size-fits-all solution, such as restricting or banning cryptocurrency usage by individuals or organizations is problematic for three major reasons. First, this is not a national problem. Blockchains exist across multiple countries and harsh regulations in a particular country or jurisdiction have little or no effect outside that country. As we have seen from other global initiatives (e.g., carbon tax proposals), it is nearly impossible to get global agreement. Second, while an important problem, cryptocurrency plays a small role in the big picture of illegal payments. Physical cash is truly anonymous and, indeed, this may account for the fact that 80.2% of the value of U.S. currency is in $100 notes. It is rare the consumers use $100 bills and it is equally rare that retailers are willing to accept them. Third, and most importantly, expunging all cryptocurrency use in a country eliminates all of the benefits of the new technology. Even further, it puts the country at a potential competitive disadvantage. For example, a ban on crypto effectively eliminates both citizens and companies from participating in web3 innovation.I would counter:
- The goal of cybercrime is not to amass cryptocurrency but fiat. Doing so involves organizations such as exchanges and banks that do respond to OFAC sanctions. The goal should be to ban the on- and off-ramps, making converting large amounts of cryptocurrency into fiat extremely difficult, risky and expensive.
- It is true that physical cash has excellent anonymity. But experts in illegal payments, such as drug smugglers, currently prefer cryptocurrency to cash as being more secure and more portable.
- This is the tell. Arguments in favor of cryptocurrencies always end up touting mythical future benefits such as "web3 innovation" to distract from the very large and very real negative externalities that they impose right now on everyone outside the crypto-bros in-group.
Cong et al divide the crimes they study into two groups:
In the first, hackers exploit weaknesses in either centralized organizations such as crypto-exchanges or decentralized algorithms, using this to siphon out cryptocurrency. For example, Mt. Gox, a Japanese crypto-exchange, was the victim of multiple attacks—the last one in 2014 led to loss of almost 850,000 bitcoins ($17b at the time of writing). In these types of attacks, coins are transferred to a blockchain address. Given that these transactions and addresses do not require real names, the attackers are initially anonymous. Indeed, the exploit is available for anyone to see given that the ledger of all transactions is public here. While the original exploit is completely anonymous (assuming the address has not been used before), the exploiter needs to somehow “cash out.” Every further transaction from that address is also public, allowing for potential deployment of blockchain forensics to track down the attacker.It is the fact that it is practically almost impossible, and theoretically unsafe, to purchase real goods with cryptocurrency that forces cybercriminals to "cash out" to fiat. Thus the need for regulators to crack down on on- and off-ramps.
They describe the second group thus:
Beyond stealing cryptocurrency via exchange and protocol exploits, traditional cybercriminal activities are now also enabled with a new payment channel using the new technology—the second opportunity our research focuses on. The use of cryptocurrencies replaces potentially traceable wire transfers or the traditional suitcase of cash, and is popular for extortion. Criminal organizations also use cryptocurrencies to launder money. According to Europol, criminals in Europe laundered approximately $125b in currency in 2018 and more than $5.5 billion through cryptocurrencies. The increasing cryptocurrency adoption also facilitates many other forms cybercrimes.Again, the authors undercut their argument against regulation by acknowledging the advantages cryptocurrencies have over "the traditional suitcase of cash". Although Cong et al briefly survey these two groups, they conclude that:
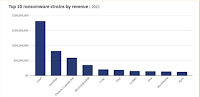
As of April 2022, Ransomware leads BTC payments with (42.5%), followed by Other (45.7%), and Bitcoin Tumbler (6.9%). If Other is excluded, Ransomware dominates cybercrime-related bitcoin activity with 86.7% of the total BTC payments.Their detailed analysis of ransomware groups' business models and operations is fascinating and well worth study. But here I want to focus on their proposal for how to combat the scourge; chain analysis. They write:
...
In light of these issues, the remainder of the article delves deeper into the economics of ransomware, the most threatening and consequential form of crypto-enabled cybercrime, to provide insights relevant for digital asset owners and investors, as well as regulatory agencies and policymakers.
While addresses are anonymous initially, funds are often transferred from one address to another in order to “cash out.” All transactions are viewable and immutable - a key feature of blockchain technology. This opens the possibility of deploying forensic tools with a focus on tracking, monitoring, and identifying the crypto transactions attributed to criminals. Indeed, our research provides a glimpse of what is possible given the transparent nature of blockchains.
 |
| Source |
One of the most troubling trends in crypto crime right now is the stunning rise in funds stolen from DeFi protocols, and in particular cross-chain bridges. Much of the value stolen from DeFi protocols can be attributed to bad actors affiliated with North Korea, especially elite hacking units like Lazarus Group. We estimate that so far in 2022, North Korea-linked groups have stolen approximately $1 billion of cryptocurrency from DeFi protocols.Plante is celebrating Chainalysis' recebt success:
With the help of law enforcement and leading organizations in the cryptocurrency industry, more than $30 million worth of cryptocurrency stolen by North Korean-linked hackers has been seized. This marks the first time ever that cryptocurrency stolen by a North Korean hacking group has been seized, and we’re confident it won’t be the last.The details are interesting but it appears that this success was enabled by regulatory action:
...
The seizures represent approximately 10% of the total funds stolen from Axie Infinity (accounting for price differences between time stolen and seized), and demonstrate that it is becoming more difficult for bad actors to successfully cash out their ill-gotten crypto gains. We have proven that with the right blockchain analysis tools, world-class investigators and compliance professionals can collaborate to stop even the most sophisticated hackers and launderers.
However, the U.S. Treasury’s Office of Foreign Assets Control (OFAC) recently sanctioned Tornado Cash for its role in laundering over $455 million worth of cryptocurrency stolen from Axie Infinity. Since then, Lazarus Group has moved away from the popular Ethereum mixer, instead leveraging DeFi services to chain hop, or switch between several different kinds of cryptocurrencies in a single transaction.Why did OFAC sanctions cause Lazarus Group to avoid Tornado Cash? It is clearly not because they were worried that sanctions would apply to them. They worried that the exchanges they need to use to "cash out" would be penalized for accepting coins trackable to one of Tornado Cash's sanctioned wallets. The exchanges need access to the global banking system to accept and distribute fiat, and that access would be at risk if they traded with a Tornado Cash wallet. Note that this would be a "strict liability" offence, so ignorance would be no excuse.
Not wishing to rain on Chainalysis' parade, but $30M is 3% of the $1B that Chainalysis estimates North Korean groups have stolen from DeFi so far this year, and 0.3% of the running total at Molly White's Web3 is going just great. Plante notes:
Much of the funds stolen from Axie Infinity remain unspent in cryptocurrency wallets under the hackers’ control. We look forward to continuing to work with the cryptocurrency ecosystem to prevent them and other illicit actors from cashing out their funds.There is clearly a long way to go before claiming that it is "Difficult for North Korean Hackers To Profit", let alone cyber criminals more generally. Despite all the focus on the blockchain, it is clear that the key vulnerability of cyber criminals is their need eventually to convert cryptocurrency into fiat. This was, for example, the undoing of Ilya Lichtenstein and Heather Morgan. Increasing regulation and its enforcement on the cryptocurrency on- and 0ff-ramps is essential.
10 comments:
David Yaffe-Bellany's The Crypto World Is on Edge After a String of Hacks describes some of the crime:
"Hackers have terrorized the crypto industry for years, stealing Bitcoin from online wallets and raiding the exchanges where investors buy and sell digital currencies. But the rapid proliferation of DeFi start-ups like Beanstalk has given rise to a new type of threat.
These loosely regulated ventures allow people to borrow, lend and conduct other transactions without banks or brokers, relying instead on a system governed by code. Using DeFi software, investors can take out loans without revealing their identities or even undergoing a credit check. As the market surged last year, the emerging sector was hailed as the future of finance, a democratic alternative to Wall Street that would give amateur traders access to more capital. Crypto users entrusted roughly $100 billion in virtual currency to hundreds of DeFi projects.
But some of the software was built on faulty code. This year, $2.2 billion in cryptocurrency has been stolen from DeFi projects, according to the crypto tracking firm Chainalysis, putting the overall industry on a pace for its worst year of hacking losses."
Willie Sutton was asked why he robbed banks, and famously answered "because that's where the money is". Now much of the money is in cryptocurrency bridges, which David Gerard described thus:
"DeFi is correctly viewed as a piñata — you whack it in the right spot, and a pile of crypto falls out. ... Bridges are the fattest piñatas in DeFi. When you see news of a crypto hack that says hundreds of millions of “dollars” were stolen, it was usually someone stealing the cryptos from a bridge."
Now, in Hackers Feast on Crypto Weak Link and Even Binance Isn’t Spared Sidhartha Shukla and Anna Irrera discuss the attraction of these bags of coins for criminals:
"There’s a gaping hole in the crypto industry’s security architecture, and even the most deep-pocked players haven’t figured out how to plug it.
The weakness in question is what’s known in industry parlance as cross-chain bridges -- software that allows crypto tokens to move between different blockchains.
On Thursday, a hacker made off with about $100 million via a bridge used by Binance Holdings Ltd., crypto’s largest exchange."
The details of the heist?
"A total of 2 million Binance Coin -- equivalent to nearly $570 million -- were effectively minted and taken by the hacker. Binance said in a statement that the incident was isolated to BNB Chain, over which it doesn’t exert control. About $100 million of the stolen funds were not recovered, while the rest were frozen, according to the statement. No user funds were lost, Binance added."
And what does this mean?
"The inability to make bridges safe -- Chainalysis estimates that $2 billion worth of tokens have been looted from 13 separate attacks, the majority of which was stolen this year -- presents a fundamental dilemma, because without such platforms, major blockchains from Ethereum to Solana remain largely segregated from each other. The vision behind web3, billed by protagonists as the internet’s next iteration, rests in part on tokens flowing freely between various ecosystems."
Perhaps it means that the Web3 hype is just unrealistic.
Crypto Hackers Set for Record Year After Looting Over $3 Billion by Sunil Jagtiani runs the numbers on this year's 125 and counting heists:
"At least $718 million has been stolen so far in October alone, taking the gross tally for the year past $3 billion and putting 2022 on course to be a record for the total value hacked, according to blockchain specialist Chainalysis Inc."
This may not be a crime, but it definitely should be. Olga Kharif reports that Crypto Slump Leaves 12,100 Coins Trapped in Zombie Trading Limbo:
"Most blockchain projects are built around bespoke digital coins, which often function as user rewards and compensate developers for their work, giving them incentive to stay involved. During last year’s price run-up, thousands of crypto startups issued new tokens to support these projects, and bullish sentiment meant there was ample demand for the market to absorb the vast majority of them and still drive prices higher.
...
Nomics compiled an analysis of coin activity for Bloomberg and discovered that more than 12,100 tokens have become “zombies” this year, defined as tokens that have not traded for a month. That’s more than twice as many as in all prior years combined, the researcher found.
...
Even among active coins, trading can be thin. Of the more than 64,400 assets Nomics tracks, only about 13,800 had trading volume in a recent 24-hour period last week, Gauthier said. And there are myriad coins that are not quite zombies yet but nearly so, and trading at a fraction of a cent"
Only 24% of Nomics coin universe traded in a day. And yet people believe the quoted "price"!
The subhead of David Voreacos' Millions in Cryptocurrency Vanished as Agents Watched Helplessly illustrates a common misconception:
"Feds locked up a storage device full of ill-gotten tokens. Then someone started stealing the loot"
And Voreacos writes:
"As authorities watched helplessly, 713 digital tokens—then worth almost $5 million—were somehow spirited away from the “hardware wallet” they were holding in an evidence locker."
The misconception is that hardware cryptocurrency wallets "contain" cryptocurrency. They don't; they contain the private halves of the key pair that validates transactions by the wallet named by the public half. Thus seizing a hardware wallet prevents transactions only if no-one knows the private key. In this case, someone did, and was able to transact from the wallets the hardware wallet was protecting. Voreacos explains:
"As a backup, Trezor hardware wallets can generate a “seed phrase,” a combination of as many as 24 words that can re-create those private keys on another device. In essence, anyone who knows the magic words and an additional PIN can take control of the Bitcoin. Unplugging the wallet device and physically locking it away is no protection."
Jack Gillum reports that US Banks Spent $1 Billion on Ransomware Payments in 2021, Treasury Says:
"US financial institutions spent nearly $1.2 billion on likely ransomware-related payments last year, most commonly in response to breaches originating with Russian criminal groups, according to the Treasury Department.
The payments more than doubled from 2020, underscoring the pernicious damage that ransomware continues to wreak on the private sector.
...
Financial institutions filed 1,489 incidents related to ransomware in 2021, up from 487 the year before, according to data collected under the Bank Secrecy Act. FinCEN’s analysis included extortion amounts, attempted transactions and payments that were unpaid.
FinCEN said the top five highest-grossing ransomware variants from the second half of 2021 are connected to Russian cybercriminals. The damage from Russian-related ransomware during that period totaled more than $219 million, according to the data."
Jessica Lyons Hardcastle's Ritz cracker giant settles bust-up with insurer over $100m+ NotPetya cleanup carries the subhead:
"Deal could 'upend the entire cyber-insurance ecosystem and make it almost impossible to get meaningful cyber coverage'"
It starts:
"Mondelez International has settled its lawsuit against Zurich American Insurance Company, which it brought because the insurer refused to cover the snack giant's $100-million-plus cleanup bill following the 2017 NotPetya outbreak.
The years-long legal battle over the claim has been closely watched by cyber-insurance and legal experts. It has helped fuel an ongoing debate over what constitutes an act of war — which even in cyberspace could invalidate an insurance claim – and whether insurance companies should pay damages caused by network intrusions supported or organized by nation states."
From the SDNY we find U.S. Attorney Announces Historic $3.36 Billion Cryptocurrency Seizure And Conviction In Connection With Silk Road Dark Web Fraud:
"JAMES ZHONG pled guilty to committing wire fraud in September 2012 when he unlawfully obtained over 50,000 Bitcoin from the Silk Road dark web internet marketplace. ZHONG pled guilty on Friday, November 4, 2022, before United States District Judge Paul G. Gardephe.
On November 9, 2021, pursuant to a judicially authorized premises search warrant of ZHONG’s Gainesville, Georgia, house, law enforcement seized approximately 50,676.17851897 Bitcoin, then valued at over $3.36 billion."
"then valued" is doing a lot of work here. The stash is currently valued at around $1.05B, which is around 2% of the daily BTC volume.
With lawyers like these, who needs crooks? Haley Hintze points to some of them in FTX collapse, Tether operations have links to infamous online-poker cheating scandals:
"Friedberg, who served as FTX’s general counsel before taking on the company’s regulatory role, was recently described by Coingeek’s Steven Stradbrooke as being “almost comically inappropriate” for the job. The description appears apt, given Friedberg’s long history of not complying with various jurisdictions’ regulations, but rather, evading them.
Friedberg isn’t even the only former UB lawyer to have found a home with a major crypto firm. Stuart Hoegner, another former UB lawyer, holds a similar regulatory-compliance post with rival crypto firm Tether, which is one of numerous trading exchanges that suffered a hit this week due to FTX’s ongoing “Alameda” problem. And a third former UB lawyer, Sanford “Sandy” Millar, operates a boutique California law firm specializing in crypto issues.
The current pastimes of the former UB lawyers represent one of the darker realities of the crypto space, in that the lightly regulated industry was a magnet to business types who already played at the edges of legality."
Coffeezilla's video This Wasn't an Accident argues that SBF is gaslighting when he claims that he "fucked up". Evidence of deliberate fraud includes:
- Appointing as general counsel and subsequently regulatory counsel a lawyer with resume including covering up an online poker cheating scandal.
- Implementing a backdoor that evaded internal checks.
- Exempting Alameda from liquidations on margin positions.
Post a Comment