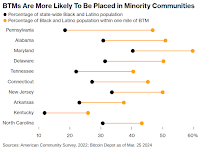
 |
| Source |
Follow me below the fold as I discuss the article and finally get to why the sting in the tail is interesting..
I'm David Rosenthal, and this is a place to discuss the work I'm doing in Digital Preservation.
 |
| Source |
It seems the driver thought that it was OK to drive home with a blood alcohol level of 0.26 because he believed Musk's hype that Fake Self Driving would handle it despite having to repeatedly override it on the way out.Now, the team's Faiz Siddiqui and Trisha Thadani are out with In 2018 crash, Tesla’s Autopilot just followed the lane lines. Below the fold I look into what it reveals about Autopilot.
 |
| Source |
 |
| @tzedonn |
There is a surprising amount of respect for people who appear to know nothing about the industry. They’re known as the “left curves.”Below the fold I look at the left side of the curve
The nickname comes from a popular meme in crypto that shows a bell curve with investors on the left who know nothing, or very little, and those in the fat middle of the curve who know something about crypto. On the right are investors who seemingly know everything.
Through blockchain addresses used by ‘‘pig butchering’’ victims, we trace crypto flows and uncover methods commonly used by scammers to obfuscate their activities, including multiple transactions, swapping between cryptocurrencies through DeFi smart contracts, and bridging across blockchains. The perpetrators interact freely with major crypto exchanges, sending over 104,000 small potential inducement payments to build trust with victims. Funds exit the crypto network in large quantities, mostly in Tether, through less transparent but large exchanges—Binance, Huobi, and OKX. These criminal enterprises pay approximately 87 basis points in transaction fees and appear to have recently moved at least $75.3 billion into suspicious exchange deposit accounts, including $15.2 billion from exchanges commonly used by U.S. investors. Our findings highlight how the ‘‘reputable’’ crypto industry provides the common gateways and exit points for massive amounts of criminal capital flows. We hope these findings will help shed light on and ultimately stop these heinous crimes.
 |
| Griffin & Wei Fig. 9 |
 |
| Source |
we increase the capacity of [optical data storage] to the petabit level by extending the planar recording architecture to three dimensions with hundreds of layers, meanwhile breaking the optical diffraction limit barrier of the recorded spots. We develop an optical recording medium based on a photoresist film doped with aggregation-induced emission dye, which can be optically stimulated by femtosecond laser beams. This film is highly transparent and uniform, and the aggregation-induced emission phenomenon provides the storage mechanism. It can also be inhibited by another deactivating beam, resulting in a recording spot with a super-resolution scale. This technology makes it possible to achieve exabit-level storage by stacking nanoscale disks into arrays, which is essential in big data centres with limited space.Below the fold I discuss this technology.